
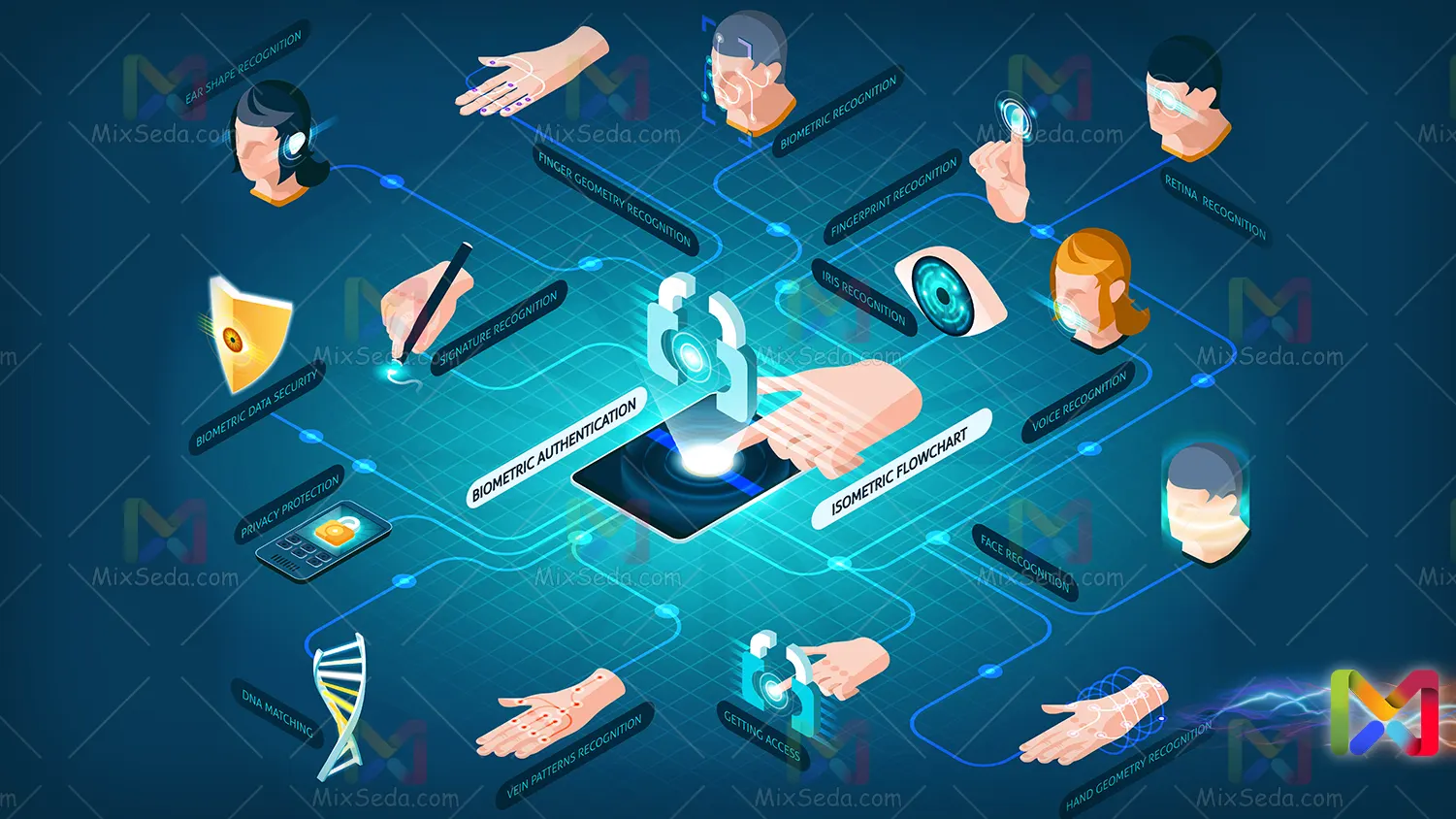
Authentication methods are methods by which a computer system authenticates you. Before we begin, I want to note that many of these elements are not part of network + and I am just explaining these elements for familiarity.
In many computer systems, you may not see many authentication methods. The reason could be related to the high cost of implementing some of these practices.
In many cases, the authentication methods applied by the user are preferable to other biometric methods. The reason for this is very clear. A system can fail in the user authentication process for various reasons, but a user is never expected to enter their password incorrectly.
For example, a number of authentication methods may be able to successfully perform the authentication process at a certain temperature and humidity. Fingerprint or fingerprint authentication cannot identify many cases if your fingers are wet.
Some authentication methods are also not very secure. For example, in today's era, most people can be seen either on their personal pages or in their conversations; Recorded the sound. It is obvious that the voice-only user authentication method cannot provide much security for systems.
Of course, we are not talking about the security of these authentication methods here, because in fact it is not possible to discuss this issue in a specialized way.
For example, a company may claim to have succeeded in creating a much more accurate fingerprint system than Iris Recognition authentication. Well, it goes without saying that the manufacturing technology of each of the items we want to talk about is different, you can always compare two items of the same type.
For example, you can compare a specific model of a face detection module with another model of this module to see which one performs better identification and which one has fewer authentication errors.
I tried to explain the most famous authentication methods to you. It goes without saying that there are many authentication methods and, moreover, some of these methods may not yet be known or may not be used in everyday life for various reasons.
Username & Password
One of the simplest and earliest authentication methods in computer systems is authentication using the Username and Password method. The truth is, I don't think I need to explain much about this because almost everyone uses this authentication method many times throughout the day.
If you remember, in the old operating systems, even in the first versions of Microsoft Windows, to access you had to enter Username and Password. After some time, the operating systems would show you the users of a computer so that you can more easily enter your user.
For example, when I was very young, I remember that we usually didn't have user accounts on some computers for some reason. For example, in schools with computers, they certainly did not allow every student to create an independent user. At the time, students used methods to hide users on operating systems such as Windows XP.
Although this was not the right thing to do, I myself preferred to have a user on every computer in the school.😊

Although the Username and Password authentication method is very old, it is considered one of the most used authentication methods. In many cases, systems use this method if they cannot authenticate you with other methods.
For example, if a system fails to identify a user using biometric authentication methods after several attempts; Will go to this method. The reason is also very personal; It is possible that an authentication method is not recognizing you correctly due to any problem.
But computer system creators expect users to be able to enter their passwords correctly if biometric authentication methods fail to identify them.
In future courses, you will also know the weaknesses of each authentication method, and I can talk about the security of these methods with this level of knowledge.
Usually, the chosen password is not stored directly or raw on computer systems and different systems try to use different hashing methods to encrypt the chosen password. Even some operating systems, such as Microsoft products, try to make the hashed password largely inaccessible.
To choose a username, you can choose limited characters in different systems and you cannot use any characters in your password. Of course, this is different in different systems.
In addition, in some cases, they take into account a number of password policies in different systems. For example, users in an organization may not be allowed to choose a 4-digit password and their password must be at least 8 characters in which upper and lower case letters are respected.
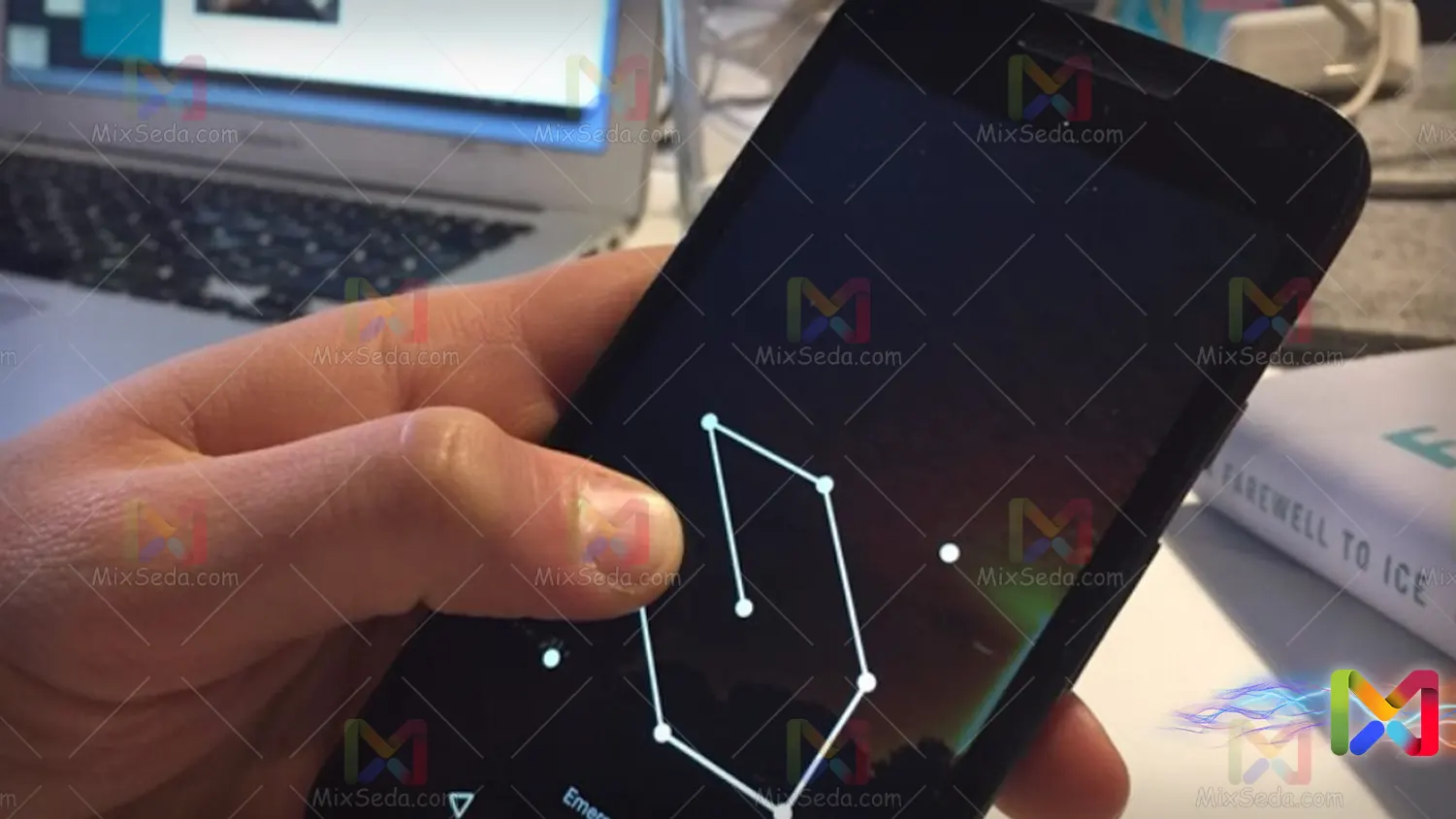
Pattern
One of the most famous methods used to access computer systems, especially smartphones with an Android operating system, is the pattern.
In this method, you enter a computer system by entering a selected pattern which is usually performed using 9 points.
One of the problems with this authentication method is that you have around 360,000 different choices for choosing a scheme, which, considering you can't choose other points from anywhere, this greatly reduces the number of your choices and as a result you will have much less security than to the Username and Password method.
On the other hand, maintaining a pattern because it has physical form can be much easier than a 9-digit number. Because of this, someone could easily mimic your model if they see it.
Usually, in Android operating systems, as far as I know, special encryption and encryption are not applied to the selected pattern, although the pattern you considered is stored in protected files, but usually Android operating systems are less secure than others operating systems systems.
In short, try not to use a diagram that contains only a 9-point chart. In some Android ROMs, you can change the number of points of these models, or the best option is to use another method for authentication.
PIN
The word Pin stands for Personal Identification Number. If you pay attention when buying phone SIM cards, you will surely see two numbers PIN and PUK. If you remember, all SIMs had PIN activated in the past and this number may have changed by Arbaran.
The reason was that if the SIM card was stolen, no one except the original owner could use it. You were forced to use the PUK by entering the wrong PIN three times.
The difference between PIN and using username and password is that you can only use numbers in your PIN. For example, one of the most common uses of the PIN during the day are bank card passwords.
You make a lot of purchases throughout the day, and in most of these purchases you use credit cards that require you to enter a PIN for authentication.
Normally, users use 4-digit numbers to select a PIN. Even in older systems you didn't have the ability to use numbers with more than 4 digits. Of course, the fewer digits you use to choose a PIN, the less security you will have in your systems.
Using 4 digits for a PIN means that you choose a mode in the range of 1000 different modes. Well, guessing a 4-digit number may not be a very difficult task for a hacker. For this reason, the PINs of the bank cards of Swiss banks are 6-digit.

In 2002, a PhD student from the University of Cambridge was able to discover a vulnerability in the PIN generation of IBM 3624 systems. The problem was that this vulnerability was found in many production hardware.
The attack related to this vulnerability, called the "decimal table attack", allows people with access to banking systems to find the credit card password in an average of 15 attempts.
The reason for using the PIN on many systems is that a username and password authentication method is not required. I mean, imagine that if you were to use the Username and Password method in ATM devices, all these devices would have to be connected to a single keyboard.
Fingerprint
Fingerprint literally means fingerprint. As you know, the fingerprints of every person in the world are unique and you will not normally find the fingerprints of two people alike.
Therefore, they try to use fingerprints and other biometric information in authentication methods. According to the research conducted, the chance that two fingerprints are similar to each other is 1 in sixty-four billion, which is almost impossible.
Fingerprints are very small bumps that are found on each person's finger. The fingerprint of each finger is also different from the other fingers, and for this reason the fingerprints of all fingers are used in the fingerprint.
Fingerprint sensors were originally developed for security locations such as secret services or military locations. These sensors were very expensive and were among the technologies that not all organizations could use.
Over time, this technology has been installed on laptops and all kinds of equipment so that users have more confidence in using them. At first, these sensors had little accuracy and exhibited a high error rate.

But over time their accuracy has increased and today, thanks to the simplicity and high safety of this technology, you can see it on all equipment. Some cars are also equipped with fingerprint sensors.
As I said above, choosing the fingerprint method in a secure digital sensor system is like choosing a password with sixty-four billion permutations. For this reason it is almost useless to produce hardware capable of testing all possible modes.
On the other hand, fingerprints can also reduce the security of devices, if someone can make a mold of your fingerprints, it makes sense that they can enter everything you have access to using the Fingerprint method.
So far, I am sure that you have realized that each authentication method has its advantages and disadvantages and because of this, different authentication methods are usually used for security places such as safes which are used for storing valuables.
Face detection
Facial recognition technology is present in many gadgets such as mobile phones. Many CCTV cameras also offer this functionality to users.
Facial recognition means that a computer system is able to identify a human face in an image and record the details of each person's face.
Face Recognition technology can offer security centers the ability to store the faces of all people at certain intervals of time. This process improves the facial recognition processes and actually allows you to compare pre-recorded faces.
Face detection generally uses the recognition of the components of a person's face, the type of positioning on the face and, in some cases, even the type of facial protrusions on a face. Then the face of each person is stored in the system memory with a series of parameters.
The first facial recognition systems had many flaws. For example, many systems were unable to recognize faces and authenticate people in bright or very low light conditions. However, with the passage of time and the introduction of more advanced products in this field, many facial recognition technologies are facing problems.
Of course, in many systems, the face detection process is included for authentication. Just like cell phones, you can perform the authentication process on all types of operating systems by setting a face.

Voice
In some Android 4 mobile phones, voice authentication was possible for users, but due to the incompleteness of this process and the ability to impersonate people's voices, this functionality has been completely removed in the following Android operating systems.
The system running the Voice process for users must be able to distinguish the sound of their surroundings from the individual's voice. In addition, you can easily hear a person's voice in the virtual space and on social pages.
Now, it is not a difficult task for a hacker to be able to mimic their own voice using a variety of computer software to fake a voice. Therefore, systems that perform the authentication process via Voice usually do not use the Voice method alone.
The Voice method authenticates by examining audio cues, recognizing the type of speech and pronunciation of words, the type of pause and amount of pauses after uttering a sentence or each word, the tone of each person's voice and the type of voice. Of course, an accurate system can never fully authenticate a user without using one or more quality microphones.
Iris Recognition
In 1983, the original idea of the separation of identity through the iris of the eye was shown in one of the James Bond films titled "Never Say Never Again". In 1987, Leonard Flom and Aran Safir; Two American ophthalmologists were able to patent this concept. But they have not been able to implement this technology.
After the patent, they went to John Daugman, who was a professor at Harvard at the time, to develop the cornea detection algorithm. In 1994 John Daugman managed to create an algorithm for detecting the cornea of the eye, which is currently the basis of all iris recognition systems.
Iris Recognition is one of the authentication methods that use biometric methods. In this method, an iris scanner (iris scan) examines the iris of the person's eye. In most of these iris scanners, infrared and visible light are used for better detection.
One of the biggest problems with Iris Recognition authentication is that with new technologies it is possible to remotely scan people's corneas. Because of this, someone may remotely scan your cornea without your consent.

Imagine what will happen if your computer password is published one day? Or even if your mobile number is posted on the Internet?
If you are not among the official officials of a country, I don't think anything will happen. You finally want to change your personal computer password or choose another phone number for your personal work. But if your biometric information is stolen for any reason, much more serious problems could occur.
The problem is that modifying biometric information is very difficult and in some cases even impossible. For example, you may be able to change your fingerprints, but what do you want to do to change the cornea of your eye? We are not talking about how iris recognition works and how corneal scanners scan, but you have to get information. Further research is possible.
Well, this article is over, but there are a lot of authentication methods that I haven't introduced for various reasons. If you know of another method for authentication, please let us know in the comments section so that I can research other methods and post the same content.
