
One of the network divisions is based on managing access to resources. Access to a network can be managed in two modes: workgroup and domain. Workgroup networks are called peer to peer and domain networks are also called client-server.
When we talk about managing access to resources in the network, it means that when our computers are networked, how they communicate with each other in terms of (logical) software.
In operating systems, we have an object called User Account, which in turn has a number of attributes. Attribute means attribute in English.
For example, the attributes of a user account can include the following:
- username
- password
- name and surname
- AND…
You will work with these attributes in general computer networking and MCSE classes.
Workgroup
When you want to create a user account on your computer, the operating system may provide you with that page and ask you to complete it.
These are the attributes of the user account you want to create.
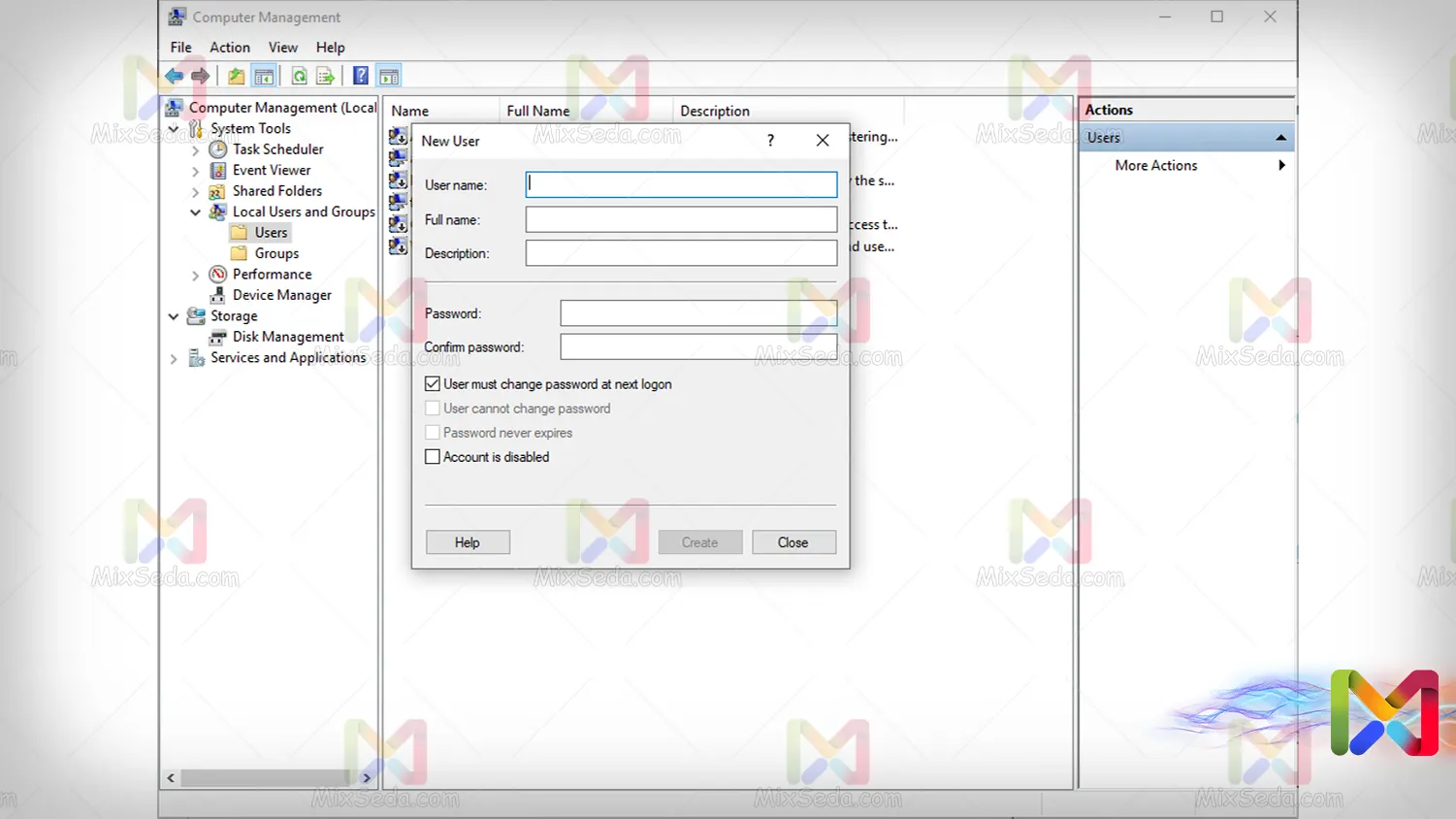
After you enter this information, this information is stored locally (on the computer itself) in workgroup networks. This information is stored in a database on the hard drive.
Database means database and it has several types. In general, databases include a series of tables that contain a series of classified information.
The database name in Microsoft Windows is LSD or Local Security Database.
This LSD is logically located in the operating system at the following address:
C:\Windows\System32\config
Perhaps you have been asked where your username and password are stored in Windows?
The answer is that your username and password along with other information are in this folder and in a file called SAM. Due to a variety of reasons, as long as the operating system is running, it cannot be viewed online.
What I mean by the word online is that you can't run this file yourself, but using a number of tools, you'll be able to make a copy of it and open that copy. (View offline)
In the Computer Management console, as in the image below, you will be able to graphically view the users created on the LSD of a computer.
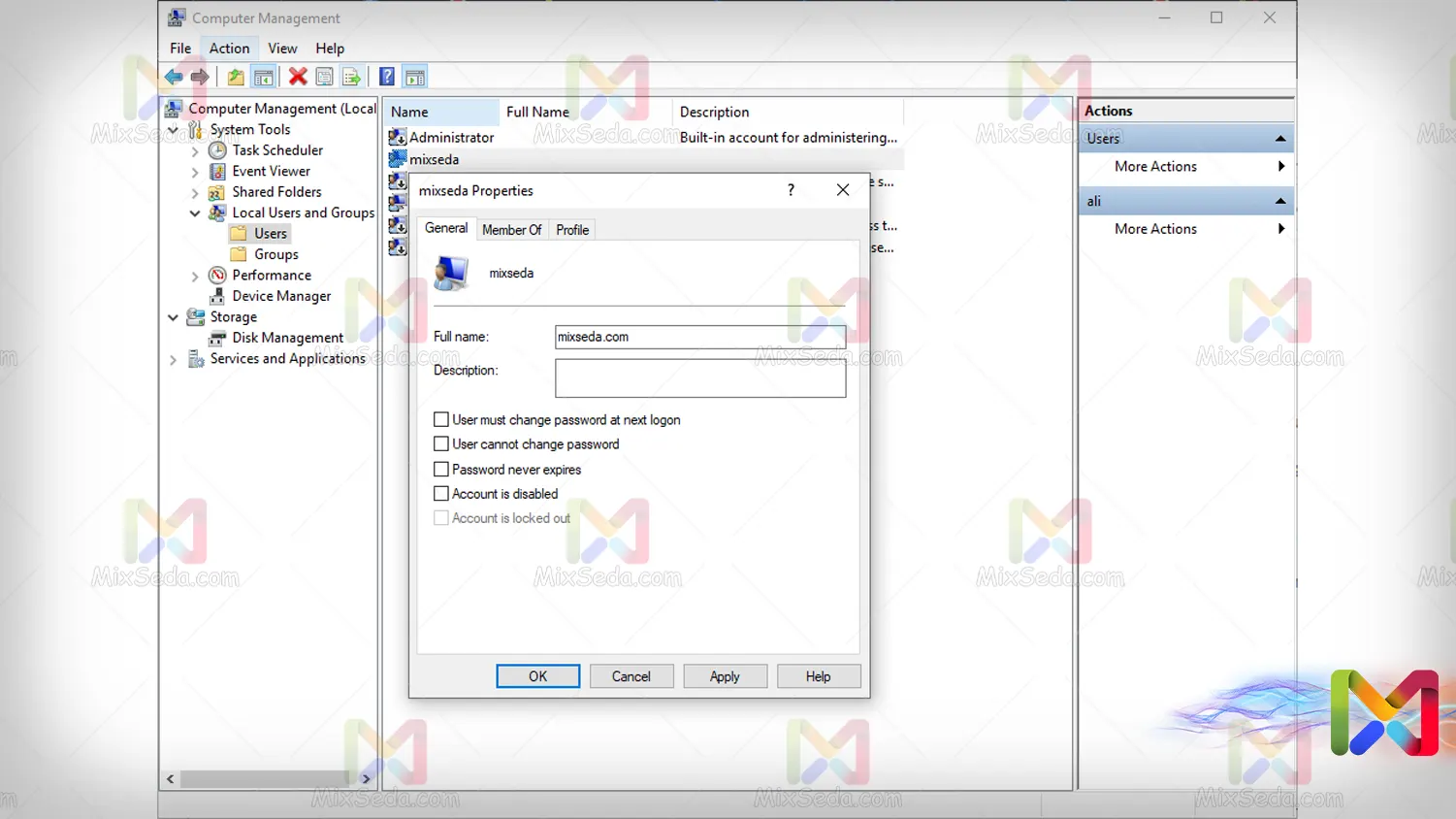
In the image above, next to some computers, an arrow may be drawn pointing down, which means that this user was created by the System itself. (integrated)
tip:
Computer Management is not a computer LSD file. In fact, you will learn in the MCSE class that Computer Management is a toolbox that helps us see a number of tools.
In the future, you can customize a toolbox in this section to have only the tools you need.
In workgroup networks, each computer (PC) has an LSD file, and each computer's LSD is stored on the same computer.
The reason we call these networks work group networks is that the management in these networks is independent and decentralized. It means that each computer manages access to itself individually.
In the workgroup network, in order to access my user account, my user account must exist in the local security database of the computer I want to access.
Now the question is: when I go through the login process on PC1, what are the steps?
Login in workgroup networks
Generally, in both workgroup networks and other networks, you have to go through three parts to log in. These three sections, which include authentication, authorization, and accounting, are called AAA, which I will give a brief explanation of here.
Authentication
Logically, when you want to log into your computer, you have to log in as a user like other users. For example, you have a vehicle and you need a key to enter this vehicle even if it is yours.
For example, I have defined a user account on PC1 including User: Wings and password: 123. Now suppose we want to enter the user account I created. The first step in logging in is authentication. Authentication means if you are really Ali and if you have permission to log into this computer or not.
For example, when you want to board the plane, your photo will be checked with your national card to see if you are really Ali Porsehi, in the next step it will be checked if Ali Porsehi is allowed to board this plane.
Now this information is written on LSD. That is, after entering the username and password, the computer checks its local security database file and checks if there is a user named Ali and password 123 on it.
Authorization
After authentication, your eligibility to access system resources is measured. In short, you are logged in, but you only have access to specific resources or you have been authorized to access these specific resources.
For example, you have been able to enter a residential unit, but are not allowed to use any facilities or enter any rooms.
Authorization topics are generally divided into the following three categories:
permission
There is a concept in the network called authorization, which determines the level of access to system resources, and this concept of authorization itself is divided into the following three categories, which are authorization levels:
- Read
- write
- Full control
Read
This type of permission is granted to you only in the case of files that you can only see, or according to the meaning of the word, you can read these files, but you will not be allowed to modify these files.
Write
This type of permission is granted to files that you can edit.
Full control
This type of permission is like having both read and write access to a file. Of course, access also includes other elements and permissions which we will explain in the future and are not the subject of our discussion at the moment.
In previous versions of Microsoft Windows, when you grant access to a file, a permission called Change is displayed. This access was the same as read and write access, but obviously Microsoft realized the error in its later versions and removed this permission.
For example, the permission defines the amount of access you have to a file, which is one of your system's resources.
Right
The right is access to the system itself. In a simpler sense, if you want to reboot a system or change system settings in the control panel or elsewhere, you will need Right access.
Now the right access permission can be issued through the operating system itself or an admin user can give you this access.
Access
The discussion of access is slightly different from Right and Authorization. Access means physical access to the hardware. When we say you have access to a server, it means your physical access to the server.
It is possible that you have the right and authorization to a computer, but you do not have access. so that you are logged into this computer from behind another computer.
In most cases, when you have Access, that is, you have access to the hardware, you can also get Rights and Permissions.
For example, if you have access to the hardware of a computer, you can change the password of this computer and define right and authorization. For this reason, server hardware is usually stored in server rooms that have security protocols and no one has the right to access them.
The authentication and authorization process is done together, that is, when a user is authenticated, he is also authorized.
This means that you shouldn't think that you have to wait for authorization after authenticating, i.e. don't think that if you run a file at the same time, since your access level has not been determined, this file will fail.
Accounting
The word accounting means auditing. This section specifies the scope of your access and your access restrictions. For example, it is assumed that you access the Internet, the volume of your Internet access can be defined with a concept called accounting.
Accounting means that a restriction has been applied to your access. Accounting itself can be defined both as Quota and Credit, which we do not intend to explain here.
I want to explain very simply, the amount of your access and the amount and volume of the access are defined by accounting.
You see this in most companies where, for example, employees have speed limits or can use a certain amount of internet volume during the day.
Communication between two computers in workgroup networks
One of the biggest drawbacks of this type of network is the lack of centralized management. If you want to access PC2 resources on a network via PC1; First, you need to go through the login process on PC1, then you need to go through the login process on PC2 again to access the resources of this computer.
In fact, for example, we must provide the user with both the authentication information on PC1 and the login information on PC2. This case doesn't cause much trouble for you in the small size.
But assuming that in a network where the user intends to connect to 10 computers for various tasks, this problem creates a lot of problems. First of all, we should provide each user with a list of users and passwords because it is difficult for ordinary users to keep such information.
Second, if a user, for example, changes their user password, a new list must be issued to inform everyone in the company again that a particular user has changed their computer password.
To solve the second problem, what can be done is to define two users on each computer, so that if the PC2 user changes his password, the PC1 user can still access the resources of this computer.
The third problem that arises in these cases is that the PC1 user can log into PC2 with the information in his possession and the username and password stored on the PC2 LSD. As a result, our network will have low security.
To solve the first problem, it is sometimes seen that the network administrator (admin) enters the same username and password of all computers to solve this problem. In this case, for reasons that will be explained later, instead of PC1 using PC2 resources, it is not necessary to complete the authentication process.
If we want to say it more correctly, the authentication process is finished, but it takes place in the background. But you will have the security problem again.
It means that each user knows the username and password of other computers and has the ability to log in and make changes on these computers. We encountered the security issue again.
This is just like installing the same lock and keys for all units within an apartment. This is truly a disaster in a network.
In the workgroup network, you will not have a limit for clients and servers, and if you want to have very normal security, you have to define user accounts on each computer as many employees as possible. If the user wants to work on a computer, his user should be defined on the LSD of this computer.
The problem that arises for you here is that if a user makes a change to one of her user attributes; You need to manually apply this change to all of these computers.
As a standard, the number of computers in a workgroup network is defined as between 2 and 10 computers. Note that I am not saying that you have a limit of 10 computers, I am saying that if there are more than this number, it will be more difficult to manage.
I suggest you think of another network if the number of your computers and servers exceeds this number.
Background Authentication
Above, I explained to you that we could run the authentication process in the background. Now we want to examine how this happens.
First of all, I want to talk about some internal parts of the computer so that you can understand this problem better. You should have an overview of RAM, CPU and hard work:
CPU
As you know, the CPU is the central processor of the computer and performs three main actions to execute the processes:
Fetch
In plain language, retrieving means asking for information. It is logical that the CPU needs a series of information for processing, it needs a series of zeros and ones.
As long as they are not 0 and 1 there is nothing to process. So, in the first step, the CPU has to retrieve this information.
Decode
Decoding is the main activity of the CPU, which means that the CPU processes the information it retrieved in the previous step.
Execute
In the final step, the decoded instructions are sent to the relevant CPU components for execution.
Hard
Your computer's main memory is hard and we won't discuss the technology and types here. The only thing that matters to us here is that Hard is slower than RAM and CPU.
This slow speed reduces the performance and efficiency of our computer.
RAM
The hard data exchange rate is much lower than the CPU processing speed. Therefore, a component called RAM was added to the computers to be placed between the hard drive and the CPU.
Suppose you work on a production line and the person in front of you is slow and your work depends on him. In this case, your work will be reduced based on that person's speed.
Now how does RAM help you?
Explaining how RAM works requires a separate article, but in summary if I want to explain; RAM uses a number of mathematical algorithms to store information you may have a lot so that you don't have to go to the hard drive every time to get this information.
As far as I know, RAM usually stores information you recently accessed and information you access frequently.
The hard drive volume in computers is much more than the RAM volume, so the RAM cannot take all the information from the hard drive and only takes the information from the hard drive that is most referenced.
Now, based on the contents we have explained, we want to switch to Background Authentication:
Assuming you are logged in on a computer with a user. In this case, the first thing that happens is that your user account is cached in the computer's RAM.
Now you want to access a file share from another computer. For this, as shown in the image below, you need to browse the IP address of the target computer in the RUN window (using the combination Win + R keys), which looks like the image below.
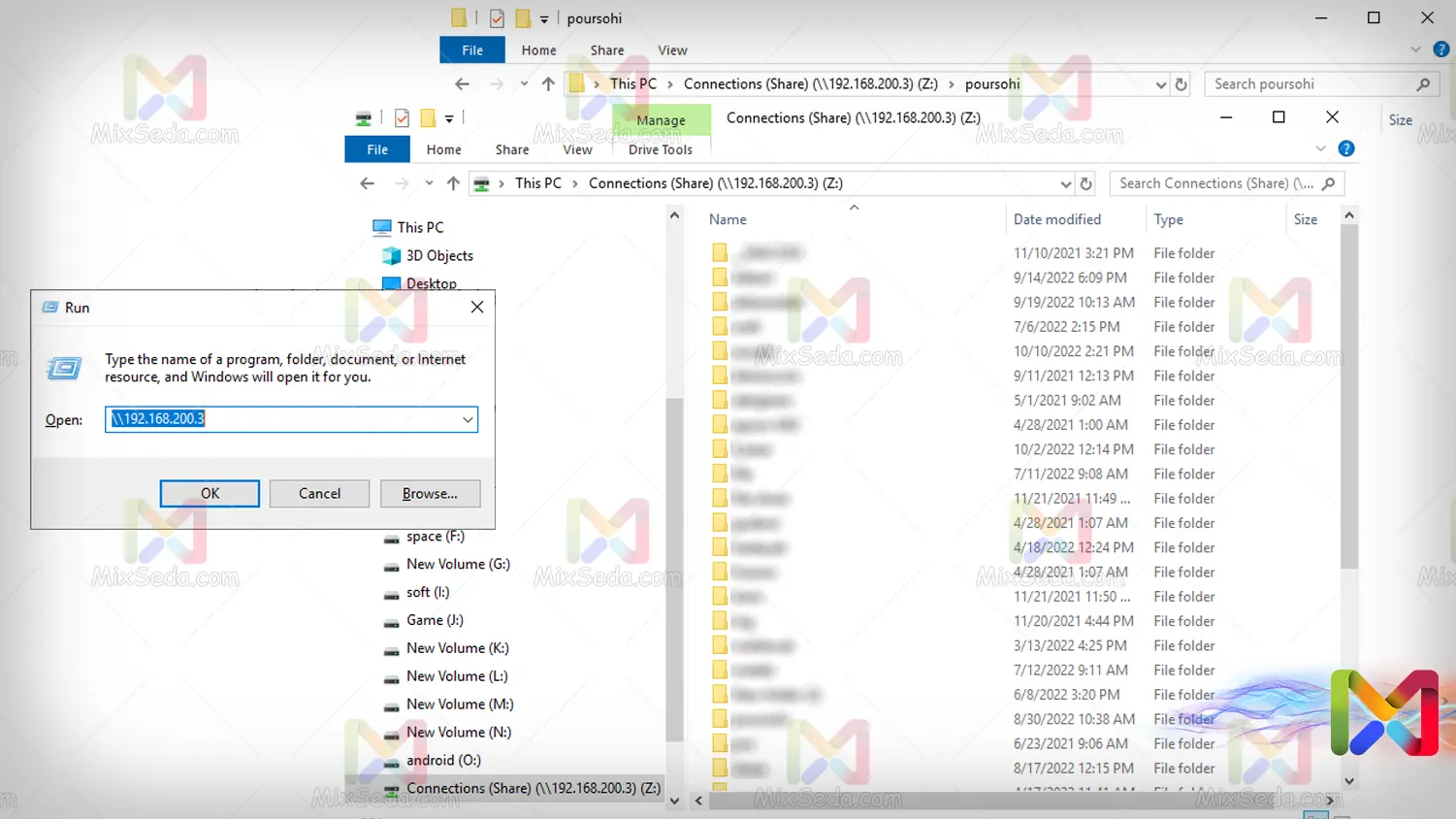
For this, you need to use two backslashes (\) and then the ip of the target computer. (Of course, there are other ways to do this.)
If your computer's username and password are the same as the target computer's, the authentication process will run in the background and will no longer authenticate your second computer.
Put simply, what happens here is that the target computer checks the cached information in the source computer's RAM to see if there is a user account it can trust.
This is the same point where we said that the network administrator has defined a unique account for each user on LSD and each of the computers in order to make her job easier.
Information exchange between two computers
The exchange of information between two computers occurs in two ways: clear txt and cipher txt. Suppose there is a middle man listening to the media on your network, this is the information that is exchanged between the computers.
In this case, if the information exchanged between two computers or in general between computers in a computer network is of type Clear txt. This person has all the information you sent to another computer.
For example, if a computer intends to send a username and password to another computer, a third party who is listening to the information sent by these two people will find out the computer's username and password.
In this case, the computers send their information as a txt cipher. Let me explain to you in plain language, they speak to each other in a different language so that no one can understand what information they are exchanging.
This event and the sending of information in the form of txt encryption are called encryption. In the discussion of encryption, we need a few things to be able to convert a clear txt into an encrypted txt.
One of these requirements is the existence of a powerful algorithm. There are many algorithms, as far as I know, all these algorithms are derived from mathematical functions.Here I will not explain the algorithms because explaining the algorithms takes time. Each algorithm has at least one key.
The existence of the algorithm alone is like an unfinished puzzle that is completed using (Key). Most of these algorithms are available on the internet and you can see how they work and their equations.
But what makes these algorithms unique between two computers is the existence of this key. Some algorithms have multiple keys.
The key is sent by the sender of the information to the recipient and the recipient of the information needs this key to break the encryption of the txt and decrypt it. This makes the third party aware of the information exchange but not of the information content.
The sender encrypts a message using the f (x) function. Then send the txt code and the algorithm key to the recipient. But this time, the recipient can decrypt the message with the inverse of the function f (x) or f '(x).
The middle man can try different types of keys to decrypt the message, this takes time but not impossible.
For this reason, keys usually have a life so that if someone learns about the key, he cannot decrypt all messages between two computers. (as a dynamic password)
Now the important question is: when will the key be sent to the target computer?
The answer is very simple, before all these tasks, these two computers establish a connection with each other via a protocol and, when this connection is established, the source computer sends the encryption key of the txt which it will send to the target computer in the future .
During communication between two computers, the key may not be sent to the target computer and only the algorithm can be specified. In this case, when sending the txt cipher itself, the key is also sent along with it.
What I have explained to you here is a very brief explanation of cryptography.To talk about this topic, you need days to fully understand such a concept.
I-land networks
One way to manage a computer network with more than 10 users is the I land method. This way, instead of having a Workgroup network, you have multiple I-lands, each of which is a Workgroup network.
This method of network management is also called an island. For example, you may have several plots of land, one of which is related to the administrative unit, another to the accounting unit, another to the control of the project, etc.
In the next step, it is best to have an administrator or help desk for each of the i-lands. Otherwise, you have to do all these things manually.
In the i-land network, there are all the problems and concerns of a network of working groups. The only thing that has happened here is that it has become easier to manage thanks to the management in the form of a computer island. But you should still do the same things you were supposed to do in the Workgroup network here in each of the i-lands.
Furthermore, the problem here is that there is no connection between the i-lands, and practically the employees of the financial unit should not have access to the computers of the administrative unit.
Of course, access can be defined, but it is not logically possible for someone from behind the computers of the financial unit; Log into the computers of the administrative unit.
You are not facing any particular complexity in Workgroup and i-land networks, although these networks cause you a lot of worry. It means that the problem of maintaining such networks is very high, but there is no special complexity in them and you can manage these networks with minimal knowledge.
So far we have found that workgroup networks are easier to implement but more difficult to manage. Furthermore, these networks have lower costs.
Domain networks
Aside from the security issues and problems it created for the network administrator, the workgroup networks had one serious weakness.
Users in workgroup networks have to keep a large number of usernames and passwords, and the biggest problem is that they have to enter these usernames and passwords every time they want to use a service.
In another sense, there is no centralized management in workgroup networks and each computer independently manages its own access. The problem with workgroup networks is that its implementation is easy and its costs are lower, but maintaining and maintaining its security is a disaster.
Centralized or domain model networks are networks that, unlike workgroup networks, are not independently managed. The solution to avoid workgroup network problems is to switch to domain networks. The point is, you need an AAA server to solve these problems.
You need a server that takes responsibility for authentication, authorization, and accounting on your network. The use of this AAA Server is that instead of each computer referencing its own LSD for each of the above actions, it refers to the AAA Server.
This AAA server has a database that stores information about each of these computers in the first step. Computers that are within the AAA server range (eg Join AAA server) should receive help from the AAA server to perform authentication, authorization, and accounting.
When a computer in the domain is active, we say that this computer is a join domain. Well, the best name that can be chosen for a domain controlling server is Domain Controller or DC for short. This is why AAA Server is called DC in networks.

On Windows Server operating systems, which currently have the best AAA servers in the world, the service this domain controller should provide to manage and control your domain is the Active Directory service.
In fact, Active Directory has all the uses of LSD to control computers. And most importantly, computers should no longer be independently controlled.
The process of authentication, administrative level determination and auditing in domain networks is almost no different from workgroup networks and the only difference is that instead of referring to LSD, computers go to the Active Directory database, called NTDS. It's DIT.
Now that the file is NTDS. How is DIT, we will talk about it in the next articles. (MCSE topics)
Now, do you think that if there is a domain in the network, another computer that is not a join domain can connect to the computers?
The answer is very simple. You can connect a computer that is not a workgroup logon domain to other computers that are a workgroup logon, but if this computer wants to access the domain controller access levels and use the Active Directory database, it must be a domain login.
I want to explain in a much simpler way, a computer that is not a join domain cannot use the Active Directory service.
DNS in domain networks
When networks were in the form of workgroups, you knew which computer you had to connect to to receive a service. But when you create a model domain network, your computer won't know where the AAA server is, so it wants to connect to another computer and receive the service after connecting to it.
For example, if you want to move to a destination for the first time, it makes sense that you don't know how to move to your destination for the first time. In this situation, a wise person takes help from Google Map or any other software to find her destination. Or he gets help from someone to help him. For example, you can call 118 to find your destination or find a number from your destination.
Now let's get back to our discussion; In computer networks, computers have to ask a server who their domain controller is and where the Active Directory service is located on my network.
The task of this work is entrusted to a server called DNS Server, whose real name is Domain Name Services. The DNS server's job is domain name resolution, which means it performs three main tasks:
- Convert IP to FQDN
- Convert FQDN to IP
- service locator
Now what is FQDN? At this point, assume that FQDN is your server name so I can explain it in the near future.
The third thing a DNS server does is what we are looking for. service locator means DNS tells you from which server each service is provided to you.
DNS should help domain-joining computers on the network so that they can find the server providing the desired service.
The difference between logon and login
Basically, these two are no different from each other. Suppose you have a house and inside this house you have a computer. When you open the door to this house and enter this house, you actually enter the interior of the house, which means that you are surrounded.
I want to explain more simply, when you sit at your computer desk and turn on your computer, you are actually logged into your operating system (OS). In the next step, when you want to access your office automation system through the browser, please go through the login procedure to access this software.

If we want to speak correctly, they log on to the computer, and logging on to the computer makes no sense. That is, to enter means to get on board, it means to be surrounded.
Login and login have nothing to do with the password; The fact that you log into your computer has nothing to do with whether or not you have a password.
