
You may think I mean hallucinogenic and psychedelic pills, but no, LSD in the computer world means local security database. In every computer (every operating system) there is a part called LSD or Local Security Database, which is responsible for keeping user information.
You may want to use a computer in a workgroup network. For this, we need to have the username and password of the computer. Well, after entering the operating system username and password, the computer checks the information we entered with its LSD.
But the importance of LSD is more than what has been said so far. LSD is a collection of user accounts, groups, security identifiers, etc. On the other hand, it can be said that any authentication and authorization process performed by the operating system in WorkGroup networks depends in some way on LSD.
If you have recently become familiar with the concept of LSD, this article may be of interest to you. Many people may be interested in knowing the computer password and think that it can be achieved by using this LSD file.
Just know that before you and me, the creators of the operating system realized the importance of the LSD file, and in addition to the protections that the operating system itself makes against LSD, even if you access the contents of these files, you won't be able to figure out the password.
Of course, there are ways to easily change the password within the LSD, but figuring out the previous password takes time and is sometimes impossible. (Impossible in the sense that this job isn't worth spending so much time on.)
LSD storage location
Well, the big question is: who is LSD ?! Where is this LSD you say ?! We see...
LSD is a concept and in different operating systems such as Windows, Mac, Android or Linux operating systems; The name and storage location are different.
Since we've all worked with Microsoft operating systems such as Windows 10, I'll start with Microsoft first.
LSD in Microsoft operating systems
On Microsoft systems, you will be able to see a file called SAM by going to "C:\Windows\system32\config". This file is the LSD in Microsoft operating systems. Of course, in the future, I may be breaking my word, but for now, consider this file as LSD.
If you want to run this file with a software to find out its contents, the following message will be displayed:
You might think that since you don't have access to this file, you can't open it or you might think it's just a permission issue.
Or you think that because this file is running, you don't have the ability to run and edit it. I am not saying that these are not cases, but the more important point is that the operating system protects these files due to its great importance.
Or rather, the operating system tells us in stupid language: "I'm too busy ... I don't want to open this file ..."
Now, how to open this SAM file which is Windows LSD?
As long as Windows is running, you can't directly open the SAM file and instead have to prepare an offline version so that you can view the information of this file over a period of time.
From Linux operating systems, you can easily log into Windows SAM and view it. Or you can copy the contents of the SAM file to a folder named sam on drive C via the following command in the command prompt with administrator access:
reg save hklm\sam c:\sam
Now, if I do that and open the final file, I will see the following images:
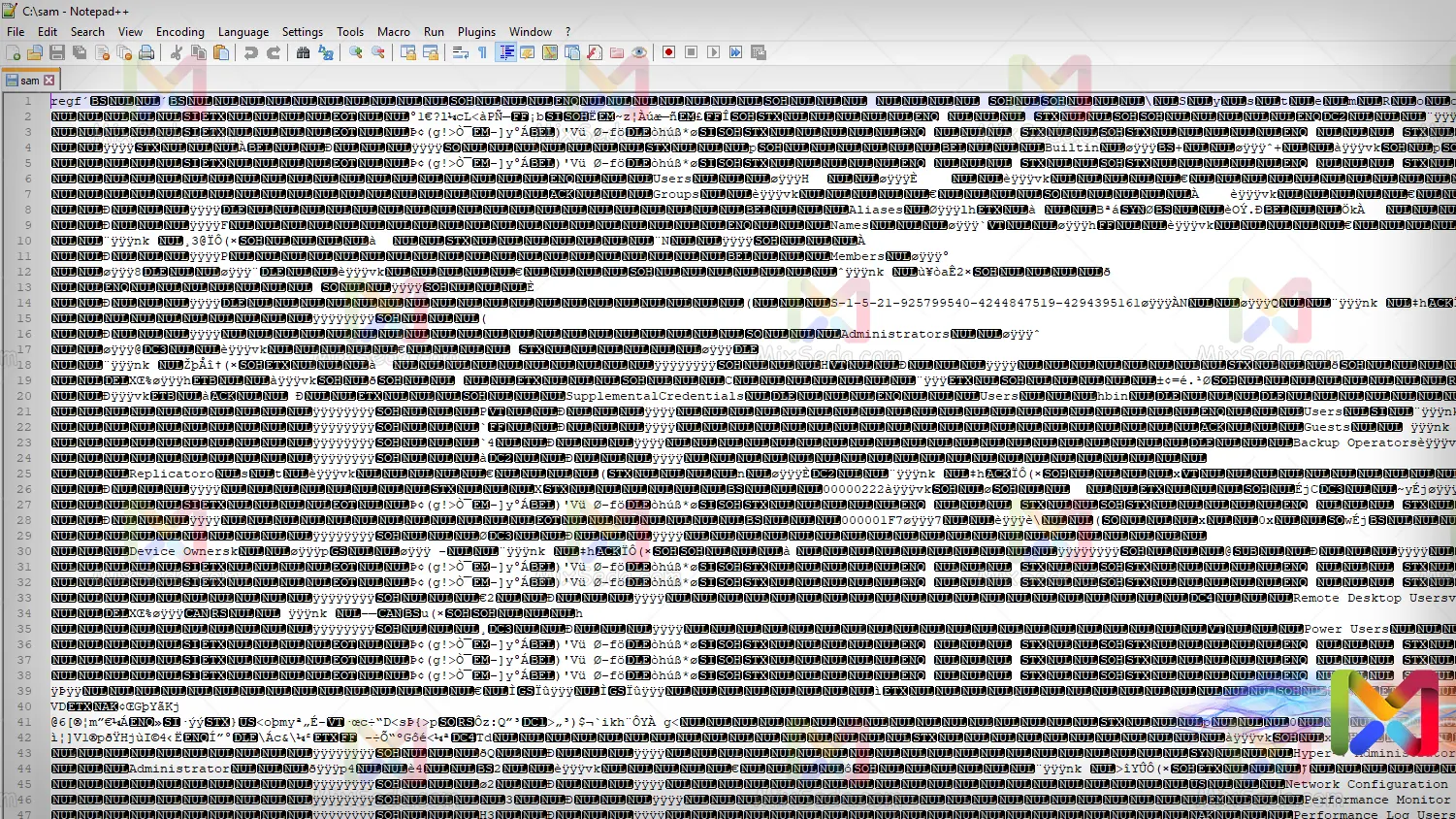
We were able to open the SAM file, but we still can't read its contents. Since special encryption is used for SAM files, don't worry. There are ways to view the exact contents of a SAM file.
In a separate article I will talk about Windows SAM extraction, because the tools to extract this file are many and extensive.
Now, if you can see the information in the Windows SAM file, you will see something in the following topics:
ali:500:aad3b435b51404eeaad3b435b51404ee:3e24dc ead23468ce597d6883c576f657:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe 0d16ae931b73c59d7e0c089c0:::userd:1000:aad3b435b51404eeaad3b435b51404ee:64f1 2cddaa88057e06a81b54e73b949b:::
The structure is such that local users of a computer are on the left side and on the other side of the password hash (Passwd hash). The question that may arise here for any beginner is what is the password hash?
Cryptography is a very big world and hashing is only a small part of it and I can't fully explain hashing in this article. If I want to look into the matter very simply, hash is an algorithm that converts a string of numbers, characters, or anything else into a character string consisting of a specific number of characters.
Exactly like what you see above in front of each user's name. These algorithms are derived from mathematics and the most important thing is that they are irreversible. That is, you can assign a file to a hash function and get a 128-bit hash, but you can't give this 128-bit hash to an algorithm and get the same file.
Hash algorithms are designed in such a way that you can almost say that you can't get the same output from two different strings.
Find a computer password from the LSD
The use of hash algorithms has increased the security of the systems, and even if you have a hashed password, you will not be able to understand it and enter the system.
That's why I told you above that changing the password and cracking it is a simple task if you have the physics of the device, or rather, you have access to a system, but it is not an easy task to find out what the other party has set the password for.
Even if the user's password is very long, it may be impossible to find it. If you want to change a Microsoft user's password, just use a tool that runs as a bootback before Windows and makes changes to the SAM file.
The number of these software and tools for this job is large and you have examples for this in Linux operating systems as well. In fact, in these software, you choose a password for a user and the software stores the chosen password in a hash form in SAM.
An example of these software is the pcunlocker software, which is used to reset the forgotten password or bypass the Windows authentication process.

But how can we find out what password a user has already entered on his computer?
For this, you need to have the hashed password of the desired user in the first two steps. If your user has complete knowledge of all types of files and computers and you don't have physical access to the target computer, it will be very difficult for you to get the password hash.
As I said, hashing algorithms are irreversible and no algorithm or software can restore them.
Assuming you get the password hash ...
In the second step, you should have a list of passwords that the user can use. The user may have used a combination of name, initials, country code, mobile number, spouse's name, year of birth, pet name, favorite device, lucky number, birthday, etc. for the password.
I mean something like this with the password list:
- 1qaz@WSX
- P@ssw0rd
- 1234
- Ali0912
- …
Now, in the next step, you need to hash all these passwords and match them with the target user's password hash, that way you will know the user's password. But if the number of characters of the user's password is too long and cannot be guessed, it may be impossible to find the password to a large extent.
Because basically, by increasing each character, the user adds a power to the passwords that you need to have in order to guess the user's password. Among them, there are sites that charge you a commission or do it for free.
These sites have already got the password hash of many passwords and by matching the entered password hash with their database, they get the final password. The important thing here is that none of these sites are so complete that they can have all the passwords. That you say you have hashed all passwords up to 10 characters is a big statement.
That's why many of these sites charge a fee to find your password. If you are familiar with the concept of permutation, you will understand what I mean.
Another point is that these sites can usually find passwords made from a combination of English characters, numbers and symbols, and I personally think it is very unlikely that they will be able to find a password that includes Persian characters on these sites.
What is the engineering password?
In network security and Microsoft courses, we are familiar with a concept called engineering password. In Microsoft courses, students usually say "P @ ssw0rd" as a Microsoft password, which means, from Microsoft's point of view, a password that contains upper and lower case letters, symbols and numbers; It will be a standard password.
Security class students usually know these two passwords as engineering passwords:
- P@ssw0rd
- Pa$$w0Rd
Of course, using these two passwords greatly reduces security, they are very predictable, and the meaning of these concepts is to use a password similar to these two passwords above. It is very important that a password be predictable and not guessable.
LSD on Linux operating systems
I don't know much about Linux operating systems and I don't work with Linux as it is known. But I had very detailed knowledge of these topics in the CEH class, which I would like to share with you.
Just as the username and passwords are transferred to the "SAM" file in Windows operating systems, there is also a local location for storing passwords in Linux operating systems. In the past, all usernames and passwords could be viewed in a file called passwd.

That is, you can easily view the contents of the passwd file and easily get the password hash using the following command in a Linux operating system:
root@mixseda:~# cat /etc/passwd
Due to a number of security issues, after a while they removed the passwords from this file and transferred them to another file called shadow. In the passwd file you can see the users, but the password is displayed with the letter X in front of each user. You will be able to see the hash of active passwords on a system using the following command and viewing the shadow file:
root@mixseda:~# cat /etc/shadow
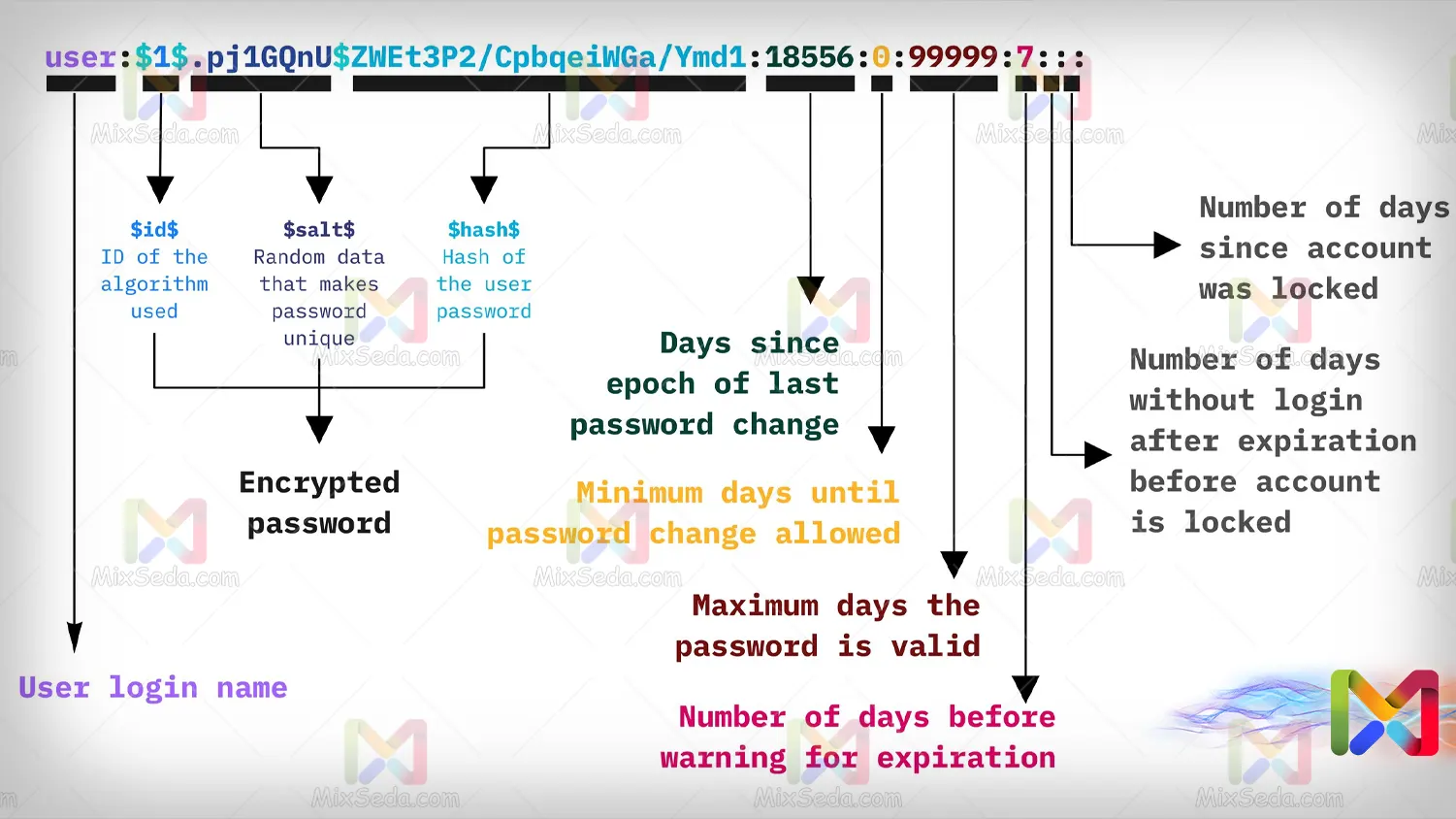
The password structure in the shadow file is designed as follows:
“Username”:“Password Hash”:“Password History”:“Minimum password life”:“Maximum password life”:“warndays”:“inactive”:“Disable time”:“Reserve”
If you take a closer look at the structure of the shadow file, it is designed exactly like a table to store user information. And each column is separated from the next column using the ":" character. Below, I intend to briefly talk about each of the concepts.
Username
The simplest concept you can understand by looking at the contents of the shadow file is the username itself. The username indicates which users exist locally on this system.
Be aware that any user in this section will not be able to log into your computer system.
Password Hash
The password set for a Linux operating system is not stored as clear text. Passwords entered in different operating systems are encrypted and hashed by irreversible algorithms.
Obviously, if a password is stored as a hash, there will be no function capable of returning this hash to the original password. Of course, there are ways to get the initial password.
In the "Hash password" section, your password is hashed in your Linux operating system. After each login and authentication; The operating system converts the entered password into a hash using algorithms and matches it with this value.
"Password Hash" itself includes the following three parts and follows the following structure:
$type$salt$hashed
Type
Type indicates the type of algorithm used for hashing. For example, for the following algorithms, the values from the following table are inserted first in the "Password Hash" value.
|
Hashing algorithm |
Type |
|
MD5 |
$1$ |
|
Blowfish |
$2a$ |
|
Eksblowfish |
$2y$ |
|
SHA-256 |
$5$ |
|
SHA-512 |
$6$ |
You may see a combination of these algorithms with some changes in a custom operating system. Or you can use other algorithms to hash the password.
Salt
Imagine that two users have the same passwords, with this description their password hashes will also be the same. Salt is a value included in the hash and makes the password hash different. Just like the seasoning you add to your food.
The existence of this amount has many advantages and is calculated by an algorithm.
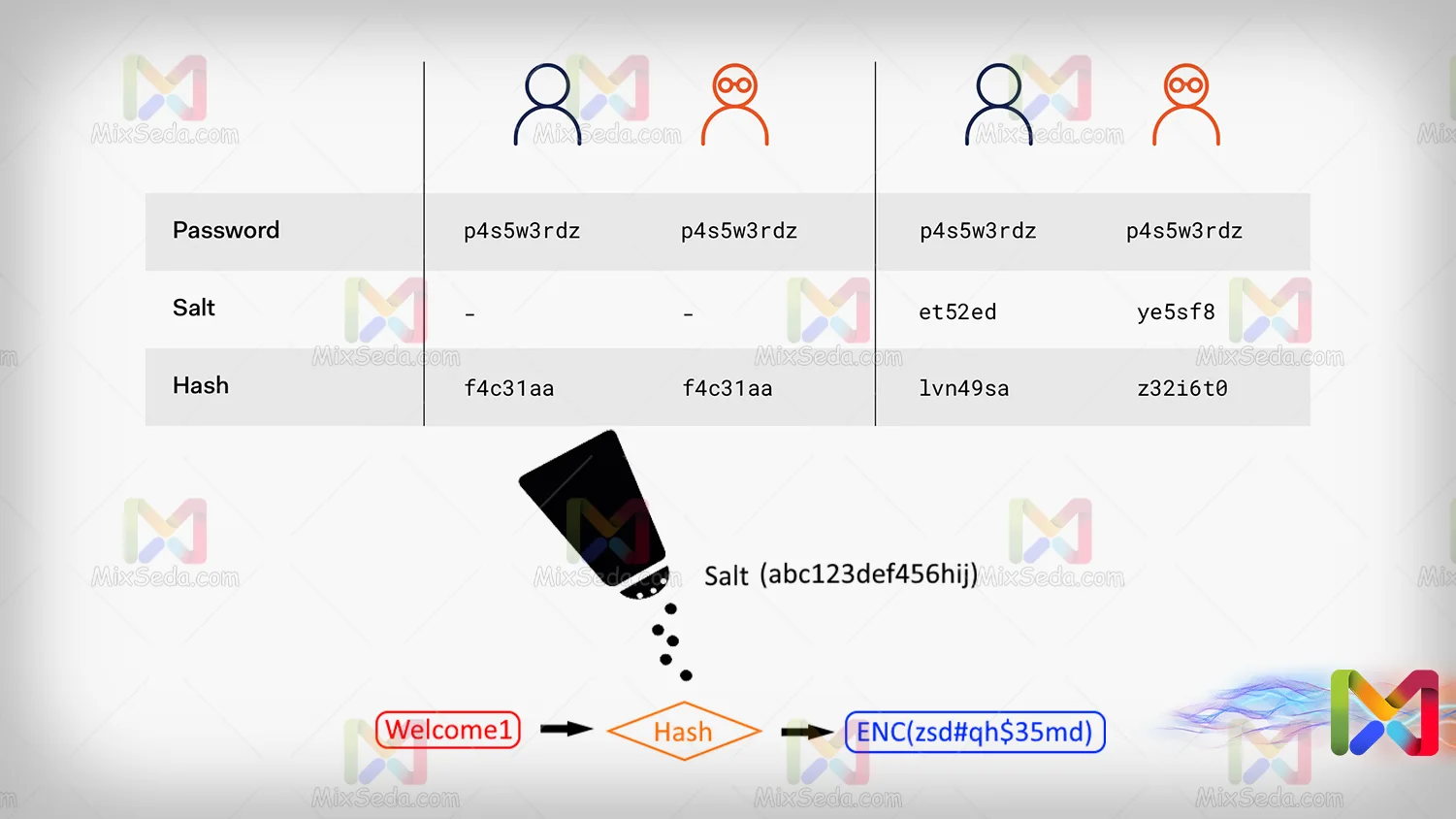
Hashed
This value is also the hash of your password, which means that according to the explanation above, your password plus the hash function with a specific salt value is equal to this value.
Password History
Password History shows the last time each username's password was changed. In fact, this value shows us the history of a password in Linux. This value is also known as "last_change".
Minimum password life
As can be seen from the name of this part, this value indicates the minimum age of the password.
Maximum password life
As in the section "Minimum password age"; The Maximum password age section determines the maximum password age assigned to the user. This value is also known as "max_age".
warndays
It is very obvious that if a password is about to expire within a certain time, the user should be informed of this first. In case of failure to notify, the user will never be able to change his password or not realize that his access is limited.
"warndas" indicates how long it takes to warn the user before the password expires.
inactive
This section shows each user's inactivity after the password has expired.
Disable time
This value indicates the number of days a user is inactive. This value is also known as "expiration".
Reserve
In many databases, programmers have come up with measures so that if you need to add a value to the database, you can easily add it.
This problem can also be found in hardware parts and most equipment, especially in the network field, has spare connectors. This can be seen in many databases.
Here, too, the "Reserve" value has such a use and its use has not yet been determined.
It is possible that if you see the shadow file on your operating system, many of the values described above may be missing. In some Linux operating systems that have been customized, such as some mobile phone operating systems, some values have been changed.
Or you might see that different algorithms are used to hash passwords in an operating system. An example of a shadow file I found on the Internet is the following:
root:$6$dSx6v.3w$NXENWxEl.eIlbCLSkbInpKpCHapHqwnyBzOxfu5R7p9zcdP4K3ucUkXZXPNbyr.rz6J9IaFQArxCa9fzXXwiW.:16835:0:99999:7:::
daemon:*:16471:0:99999:7:::
bin:*:16471:0:99999:7:::
sys:*:16471:0:99999:7:::
sync:*:16471:0:99999:7:::
games:*:16471:0:99999:7:::
man:*:16471:0:99999:7:::
lp:*:16471:0:99999:7:::
mail:*:16471:0:99999:7:::
news:*:16471:0:99999:7:::
uucp:*:16471:0:99999:7:::
proxy:*:16471:0:99999:7:::
www-data:*:16471:0:99999:7:::
backup:*:16471:0:99999:7:::
list:*:16471:0:99999:7:::
irc:*:16471:0:99999:7:::
gnats:*:16471:0:99999:7:::
nobody:*:16471:0:99999:7:::
libuuid:!:16471:0:99999:7:::
mysql:!:16471:0:99999:7:::
colord:*:16471:0:99999:7:::
usbmux:*:16471:0:99999:7:::
miredo:*:16471:0:99999:7:::
ntp:*:16471:0:99999:7:::
Debian-exim:!:16471:0:99999:7:::
arpwatch:!:16471:0:99999:7:::
avahi:*:16471:0:99999:7:::
beef-xss:*:16471:0:99999:7:::
dradis:*:16471:0:99999:7:::
pulse:*:16471:0:99999:7:::
speech-dispatcher:!:16471:0:99999:7:::
haldaemon:*:16471:0:99999:7:::
sshd:*:16471:0:99999:7:::
snmp:*:16471:0:99999:7:::
iodine:*:16471:0:99999:7:::
postgres:*:16471:0:99999:7:::
redsocks:!:16471:0:99999:7:::
stunnel4:!:16471:0:99999:7:::
statd:*:16471:0:99999:7:::
sslh:!:16471:0:99999:7:::
Debian-gdm:*:16471:0:99999:7:::
rtkit:*:16471:0:99999:7:::
saned:*:16471:0:99999:7:::
There is a lot to be said about groups in Linux operating systems, but for now you should know that the storage location of groups in Linux operating systems is in a file called group and you will be able to view it with the following command. :
root@mixseda:~# cat /etc/group
Groups in Linux operating systems have a simpler structure and usually use the following structure:
“groupname”:“x”:“group_ID”:“[username[,username]...]”
I briefly explain each of these values in the table below:
|
value |
explanation |
|
groupname |
The name of the defined group |
|
x |
Group password (not supported in some operating systems) |
|
group_ID |
The unique identifier of the group |
|
username |
Usernames belonging to this group |
