
SID stands for security identifiers. In Windows operating systems, there are identifiers called SIDs, which actually determine the security level of users and groups. In the first operating systems created by Microsoft there was no user.
After the introduction of Windows Vista, Microsoft established a concept called users on its operating systems that distinguished users from each other. At the beginning of the work, there were only two users called guest and admin, obviously, the admin user access was greater than now.
With the development of operating systems and their updates, over time, Microsoft has decided to reduce administrator access. Usually, in computer networks, due to the existence of a number of security problems, they try not to have a user with administrator access level.
Or maybe you have also heard that in os hardening they say that you should disable admin user to increase the security of your system. Microsoft has done its best in new versions of Windows to not allow access to an admin program as much as possible.
If you need to get administrator access for the program, you can only get this access to run that program using Run as administrator. Something similar to the Linux world where you normally use normal users and for jobs that require root access, you get higher access using sudo.
There are some security concepts, like user context, that I don't want to talk about right now, but you can read more articles in English. (Regarding what level a program is running at when it is run on Windows.)
Before you want to give any further explanation on SIDs, it's best to have an introduction to standard and default Microsoft Windows users and groups.
Built-in Users & Groups
We have a number of users and groups integrated into Microsoft products. Integrated means that when you install Windows, Windows automatically creates these users. For example, in Windows, if you pay attention to the Description section or the instructions of the administrator user, Built-In is written.
When installing Windows, the operating system itself creates a large number of groups and users as integrated. In the future, you can install software that will create a user or group to perform specific tasks. You use the lusrmgr console. msc you can view users and groups in your operating system.
Just use the WIN + R combination keys and type lusrmgr. msc in the Run window, open the lusrmgr console.
As for built-in groups, I'm just saying this to learn that these groups themselves are divided into two categories:
Local built-in groups are groups created by the operating system and you can view them or make a user a member of these groups. In system-integrated groups, you can view these groups in the lusrmgr console. You are not msc.
You will also learn in the future that you cannot change the structure and permissions of System Built-in groups. In fact, these groups are groups used by the operating system itself and you don't have permission to change them. You may think that in Windows operating systems, the administrator is the highest access level, but it is good to know that the system has the highest access level.
Next, I'll explain each of these groups:
Local Built-in Groups
As explained above, Local Built-in groups are groups created by the operating system itself or not created by the user. You can create a user and become a member of these groups. Depending on the version of the operating system, some of these groups may not be available on the system.
Administrators Groups
Members of the administrators group are the users who have access to the most powerful user level. It can almost be said that the members of this group have received a lot of powers from the operating system. In addition to the permissions they have, members of the administrators group can also grant access to other users and groups.
It can be said that members of the administrators group have all access available.
Users Group
This group is generally designed for users who should have limited access. For example, the users of a small company are usually part of the user group. The user group does not have permission to install the software on the operating system and, if necessary, must have the password of one of the users in the administrators group.
Replicator Group
Replica means replication. Replication in Domain mode networks transfers information between server and client. Replication is defined for many services. There are several types of replicas that you can read more about on the internet.
In domains there is a feature called directory replication, why and how it works will be explained to you in Microsoft's MCSE classes. On domain networks, users who start the replication service must be members of this group.
By default, no users are a member of the Replicator group and this group is created for directory replication access only.
Backup Operators Group
As you know, one of the most important processes in operating systems, both Windows and non-Windows, is the backup process. The Backup Operators group is created so that a user wants to make a backup copy of system files.
In many cases, a user does not do this manually and you add a user to this group and provide their information to the software to prepare a support release. The Backup Operators group does not have a default member such as the Replicator group.
Members of the Backup Operators group can back up NTFS file systems even if they do not have access to them. You can use the Backup utility software to perform backup jobs.
Event Log Readers Group
One of the things that every system, such as routers and switches, needs, and is given a lot of importance in medium to large organizations, is the issue of keeping records and recording systems and services.
In CEH classes, the last step in hacking a system is clearly tracing or clearing traces, and most of this includes clearing a system's logs. For this reason, in organizations and large networks, various systems are implemented for record maintenance and logging operations.
Users who join the Event Log Readers group can read the logs of a system. The process of reading and analyzing logs is considered a specialty in the world of networks. Of course, in small projects, many software can help you in this area.
In criminology topics that you will surely become familiar with in the future, analyzing the logs and performing registration processes in different ways is one of the important tasks. By default, no members are assigned to the Event Log Readers group.
Guests Group
The major group has very limited access to a system. This group appears in most operating systems or even in user management systems such as home modem systems. The purpose of creating this group is that if you want to give access to a user who is not a member of your network, enable this access level for him.
Usually, in networks, due to the existence of security risks, an attempt is made not to have a user with the access level of the Guest Group. If you want to make a user a member of the Guests group, it's best to create a group with specific permissions and then make the desired user a member of that group.
By default, in new Microsoft operating systems, the Guest user is a member of the Guests group.
Power Users Group
The Microsoft company tries to maintain backward compatibility not only in the supply of Windows products, but also in the supply of all its products. For example, in the same replication discussion we explained, Microsoft tried to provide communication between the old and new versions of the services.
Or in general, Microsoft products have always tried to ensure that new versions of a software have the ability to support the outputs of the old version. From Windows 7 onwards, the Power Users group was created to allow computers running Windows XP to access a folder in another Windows to retain access to it.
Remote Desktop Users Group
I think many people are familiar with Remote Desktop Service. This service allows users of Windows operating systems to remotely control a computer on a computer network.
In fact, Remote Desktop is a software-like remote service like ANYDESK, with the difference that in Remote Desktop the speed and quality of service is higher and you don't necessarily need the Internet to use it.
We can talk about the advantages and disadvantages of Remote Desktop and its protocol in general, the issue that is important to us here is that members of the Remote Desktop Users group are able to connect to a remote computer using the Remote Desktop service.
In fact, if we want to be more precise, the members of the Remote Desktop Users Group are able to access a computer remotely.
Performance Monitor Users Group
Sometimes you may have noticed the slow speed of your computer. Usually, people facing a decrease in the speed of their system check the performance of their system using tools like task manager or more professional tools.
The system performance check allows you to understand how much of the system processing volume is involved in which function and process. In larger networks, you don't have the ability to log into any systems and check system performance in case of problems.
There are software and tools for this task that actually do Performance Monitor for you. One such tool is PerfMon, which you can run using the run window in Windows.
In this article, I will not talk about the performance of these software. The only thing you need to know in this section is that users who are members of the Performance Monitor user group have the ability to access system performance.
Members of this group can sit directly behind a computer system and access system performance information or view or collect this information remotely.
Usually, in networks with adequate facilities, this information is collected and stored remotely so that, in the event of a problem, the source of the problem can be found.
IIS_IUSRS Group
IIS stands for Internet Information Service and is a web server designed and provided by Microsoft. In fact, this web server is one of the simplest and easiest web servers in my opinion. The first version of IIS was for Windows NT version 3.51.
As you know, Windows NT is one of the oldest operating systems and after Windows NT we have just seen Microsoft's Windows 2000. The iis web server information services use IIS_IUSRS group access.
Network Configuration Operators Group
In computer networks, one of the things needed to network several computers together is the network configuration. In fact, setting of IP, subnetting, dns, etc. on computers is one of the first things you need to do to network multiple computers.
Here, we have nothing to do with whether your network is a workgroup or a domain. To set up a computer's network card, you can access the change adapter setup section from the control panel or use the run window and ncpa console. Open the cpl.
Members of the Network Configuration Operators group have the ability to configure and manage computer networks. Members of this group can change a computer's network settings (such as TCP / IP settings).
Distributed COM Users Group
The first question that can occupy anyone's mind is what is Distributed COM and what is it for?
Distributed COM or Dcom is a protocol that allows direct communication of software elements on a network. Of course, the name of this protocol was OLE Network, but after some time it was changed to Distributed COM. This protocol also uses port 135.
In the future we will talk about protocols and their port numbers. Here, you just need to know that every protocol in the computer world uses one or more unique ports and in fact, by using these ports, a protocol in two computers can communicate with each other.
There is a lot of discussion about COM and its function, but in short, it can be said that Microsoft created this protocol to create a communication layer under the com + server. And the purpose of Distributed COM is to create this communication in a distributed way.
On computers, users who are members of the Distributed COM Users group have the ability to activate and run distributed COM elements. Of course, this group has no members by default.
Cryptographic Operators Group
In the future and in the topics related to information security, we will talk about cryptography. Currently, at this level of knowledge, it is a bit difficult to explain this content and to explain it I have to explain many concepts to you.
For now, you know about cryptography to such an extent that most operating systems run cryptographic processes based on their functionality.
Members of the cryptographic operators group have the ability to access or perform covert operations on the computer. And like many of the groups we've explained above, this group has no members by default.
Hyper-V Administrators
In MCSE courses you will learn about another Microsoft service called Hyper-V. This service is used for virtualization like VMware ESXI. Of course, currently, as far as I know, products like ESXI are more powerful than Hyper-V.
The Hyper-V Administrators group is related to the Hyper-V service and we will discuss this group in future MCSE tutorials.
System Built-in Groups
The members of the groups built into the system have specific criteria and criteria. Another feature of these groups is that via the lusrmgr console. msc cannot be managed, but the network administrator can use these groups to manage network resources.
Many of the concepts I explain here are just for familiarity and better learning. You will be introduced to these groups in MCSE classes. So it doesn't matter if you don't understand the significance of some of these groups which I will explain below.
Creator Owner
Creator Owner simply indicates the owner of data or processes in Windows operating systems. For example, if the mixseda user creates a folder on their desktop, the Creator Owner is considered a folder. If you create a backup job on your computer, you are the Creator Owner of that job.
In fact, the use of Creator Owner serves to specify the exact ownership of a process or data in Microsoft operating systems. When you read the permissions of the Windows OS and try them one by one, you will understand the Creator Owner concept.
Actually, as a user in Windows operating systems, since I am the owner and Creator Owner of a file, I have the ability to perform certain activities on that file. without having permission for that file. Of course, this is not an accurate explanation, but I think it suffices.
Everyone
Everyone who can access your computer belongs to the Everyone group. If you grant Everyone access to a process or file, all users can access that process or data.
If your computer joins a domain and you've granted everyone access to a file; Anyone who has joined that domain can view your file. The Everyone group is very similar to a type of group called Users in the Linux world.
Interactive
Users who consume resources on a local system are members of that system's interactive group.
Network
when accessing system resources via computer networks; You are part of the Network group.
Authenticated Users
Authenticated users, as the name suggests, includes all users who use authentic authentication methods for a computer; have had access to it.
I want to explain this concept very easily, every user logged into a computer is considered an authenticated user.
Logon Anonymous
When computers receive a service anonymously and without server authentication, we say that this service is provided anonymously to the computers. When people enter or log on to a computer system without having a valid user account, they are included in the Anonymous Access group.
Indeed, many services such as web services and ... in our network can be provided anonymously. Or someone might for some reason create an FTP on their network that they can connect to anonymously. Of course, this is wrong, but it can be given as an example.
Another thing you should know about this Anonymous Access group is that in the past the members of this group were also among the subsets of the Everyone group. But from the second Windows XP Service Pack (XP SP2) onwards, Microsoft has decided to separate this group from Everyone.
Batch
At this point you must be familiar with Batch files; Batch files are called files with the extension. bat and run on any operating system. Typically, in computer networks, we use these files to configure computers or implement a process on a large number of computers.
The batch group on computers includes users who log in to batch to perform executive operations. In fact, you shouldn't be doing a lot of things on all computers in computer networks.
For example, if you want to set up a file share on all computers in an organization, you definitely won't be logging into each of these computers, because if this organization only has 1000 computers, you could have nightmares for a long time 😊.
Instead, you can define a batch file that runs on any computer and performs the tasks related to creating the file share for you on that computer. Now, as for the same batch file, you can go to the computers one by one or you can define a process so that this batch file is run on all computers at a certain time.
Dial-up
Dial-up was a very old system that may still be used on some computers. If you remember, the computer's Internet was dial-up. That is, you had to dial a number using software or a tool to connect to the Internet.
In fact, dial-up can be a communication solution between computers on the network. Members of the remote access group are users who log on to the computer through remote access.
Service
In the future, you will become familiar with a number of services on servers that users must complete the authentication process to receive these services. The set of user accounts that log on to the computer to receive or run a service are included in the Service group.
System
This group is used by the operating system itself. As far as I know, System or Local System is considered the most powerful access group and has full access to the entire computer system. On the other hand, when a hacker infiltrates a computer system under Windows, he tries to improve his access to the system.
If a service or process can access the local system group and run with its access, that service will have access to all processes and permissions. Therefore, if a hacker can perform the desired operation with access to the system group, there is nothing to prevent it.
On Microsoft Windows operating systems, some processes and services run by default with access to the System group.
There may be groups here that I haven't covered. Of course, you will not be familiar with all of these groups on the net plus, but I prefer to express all the concepts in full in each article.
Default value of SIDs
Well, back to our discussion of SIDs:
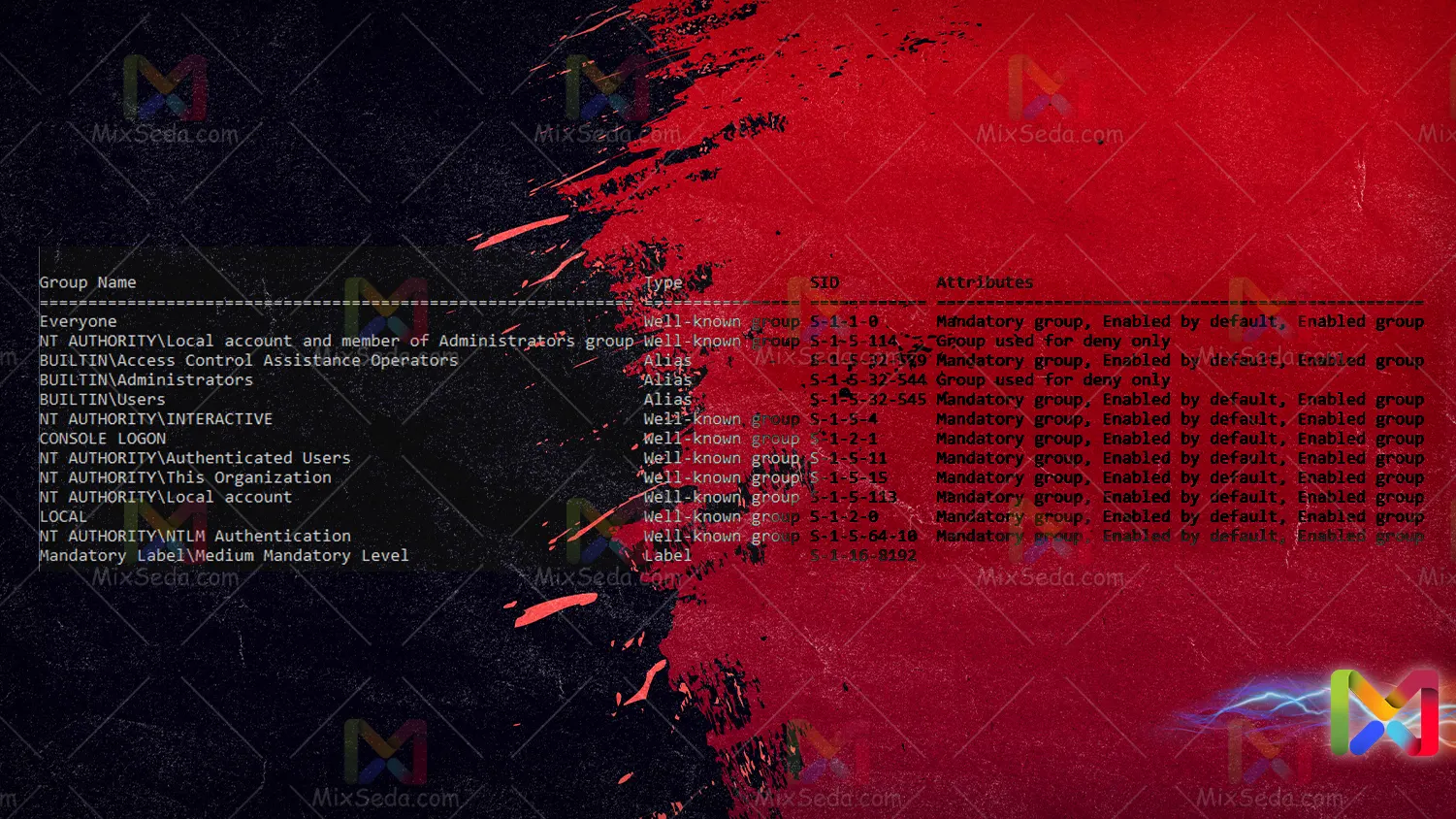
When I have access of any kind on a computer, an access level has finally become personal to me and this access level in the Microsoft Windows world is defined for me using a SID. You can view the user's SID by using the whoami / all command in the command prompt.
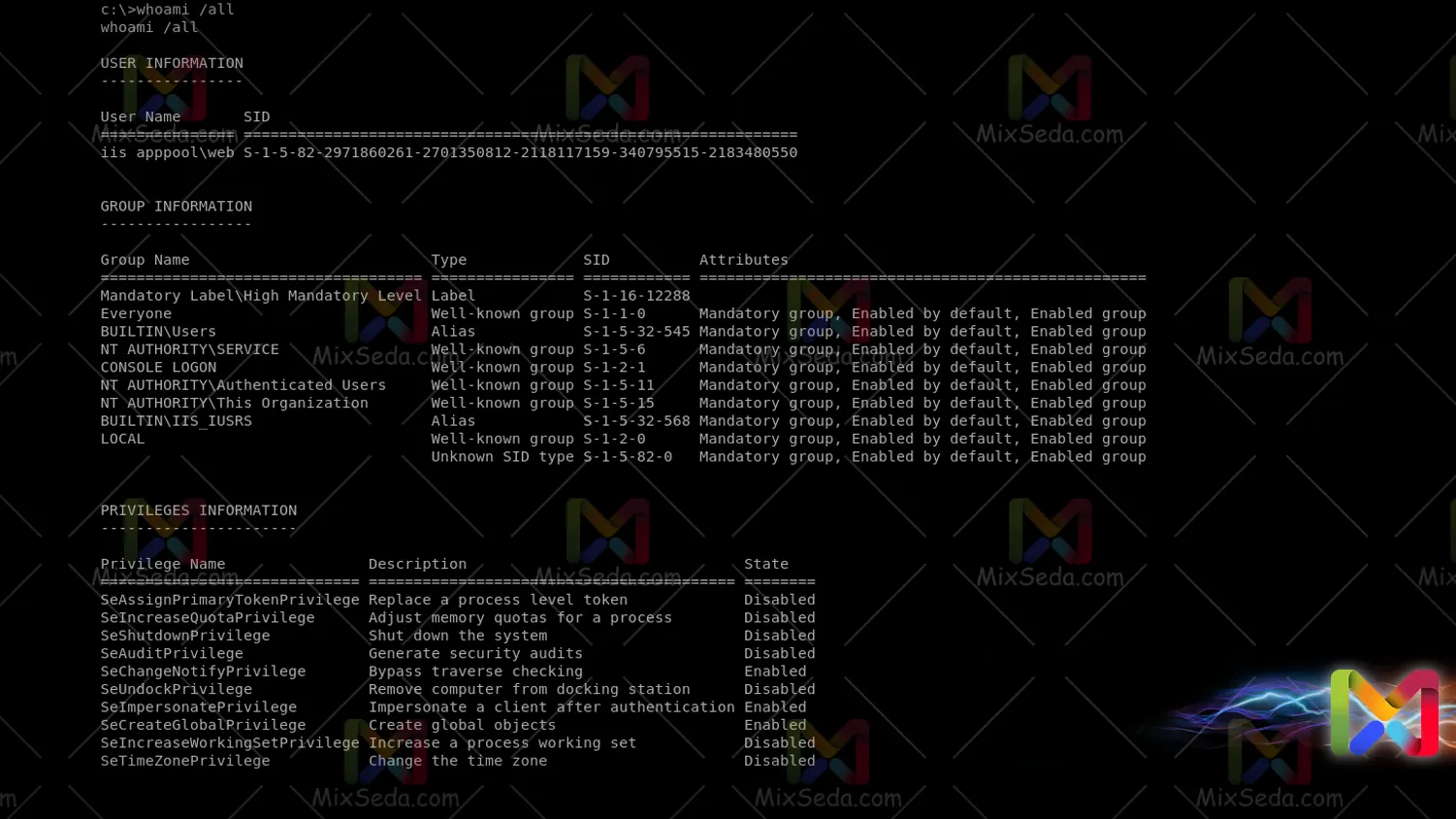
Also, if you pay attention, you will be able to see the SID of your system groups. SID is what makes a user unique. In fact, if you create two users with the same username, the same login and the same password in your network, the SID will distinguish them from each other.
A series of SIDs is called a known. For example, in all Windows operating systems, you can see that the Everyone group's SID is as follows:
S-1-1-0
Or that on all computers the local group has this structure for SID:
S-1-2-0
A very interesting point written in the CEH version 9 book on SIDs is that you have an access level on each computer before you log in. And this access level includes a SID, and this SID follows the following structure on all computers:
S-1-5-18
Another example of a SID is Null SID, which follows the following structure:
S-1-0-0
We have a number of famous SIDs, usually people who have been working in Microsoft networks for several years are familiar with these SIDs:
|
Row |
SID name |
SID value |
Description |
|
1 |
Null SID |
S-1-0-0 |
Null SID means a group that has no members. |
|
2 |
Everyone |
S-1-1-0 |
A group that includes all users except Logon Anonymous. |
|
3 |
Local |
S-1-2-0 |
This group is related to users who use the system locally. |
|
4 |
Creator Owner ID |
S-1-3-0 |
This group is created by the user by creating a process, element or file, and it shows the user's ownership of the file or process. |
|
5 |
Creator Group ID |
S-1-3-1 |
This SID is replaced by creating an element by a group. |
|
6 |
Enterprise Domain Controllers |
S-1-5-9 |
|
|
7 |
Authenticated Users |
S-1-5-11 |
|
|
8 |
Domain Admins |
S-1-5-21 |
|
|
9 |
Users |
S-1-5-32-545 |
|
|
10 |
Guests |
S-1-5-32-546 |
|
|
11 |
Account Operators |
S-1-5-32-548 |
|
|
12 |
Server Operators |
S-1-5-32-549 |
|
|
13 |
Print Operators |
S-1-5-32-550 |
|
|
14 |
Backup Operators |
S-1-5-32-551 |
|
|
15 |
Replicators |
S-1-5-32-552 |
|
|
16 |
Remote Desktop Users |
S-1-5-32-555 |
|
|
17 |
Network Configuration Operators |
S-1-5-32-556 |
|
|
18 |
Incoming Forest Trust Builders |
S-1-5-32-557 |
|
|
19 |
Event Log Readers |
S-1-5-32-573 |
|
Of course, there are many other cases that are not mentioned here, but they are explained in the SID security related books above.
If you remember, we talked about SAM or the security account manager in the last session. It is good to know that SAM stores data on SIDs. You can see many SID structures for different groups using the same command: whoami / all.
SID structure
The SID itself contains a structure. The meaning of Shhdar is that this identifier is not just a series of random characters and a series of concepts can be reached from the SID itself. For example, consider the following SID:
S-1-5-21-925799540-4244847519-4294395161-1000
SIDs have three main parts in terms of structure:
The leading part of the SID, which is equivalent to S-1-5-21, indicates the SID group. For example, if two users have the same groups, their initial part is also the same, such as the following two SIDs:
S-1-5-21-925799540-4244847519-4294395161-1000S-1-5-21-549688327-91903405-2500298261-1000
The second part is related to the domain, which we don't want to explain much here. When a domain is created, part of the SID is the same for all computers that join that domain. In the SID we gave an example above, the part "925799540-4244847519-4294395161" is related to this section.
The most important part that makes up a SID is the relative identifier, also called relative ID or RID for short. In fact, this section contains a number that distinguishes each user from another user. That is, in fact, users are identified through RID.
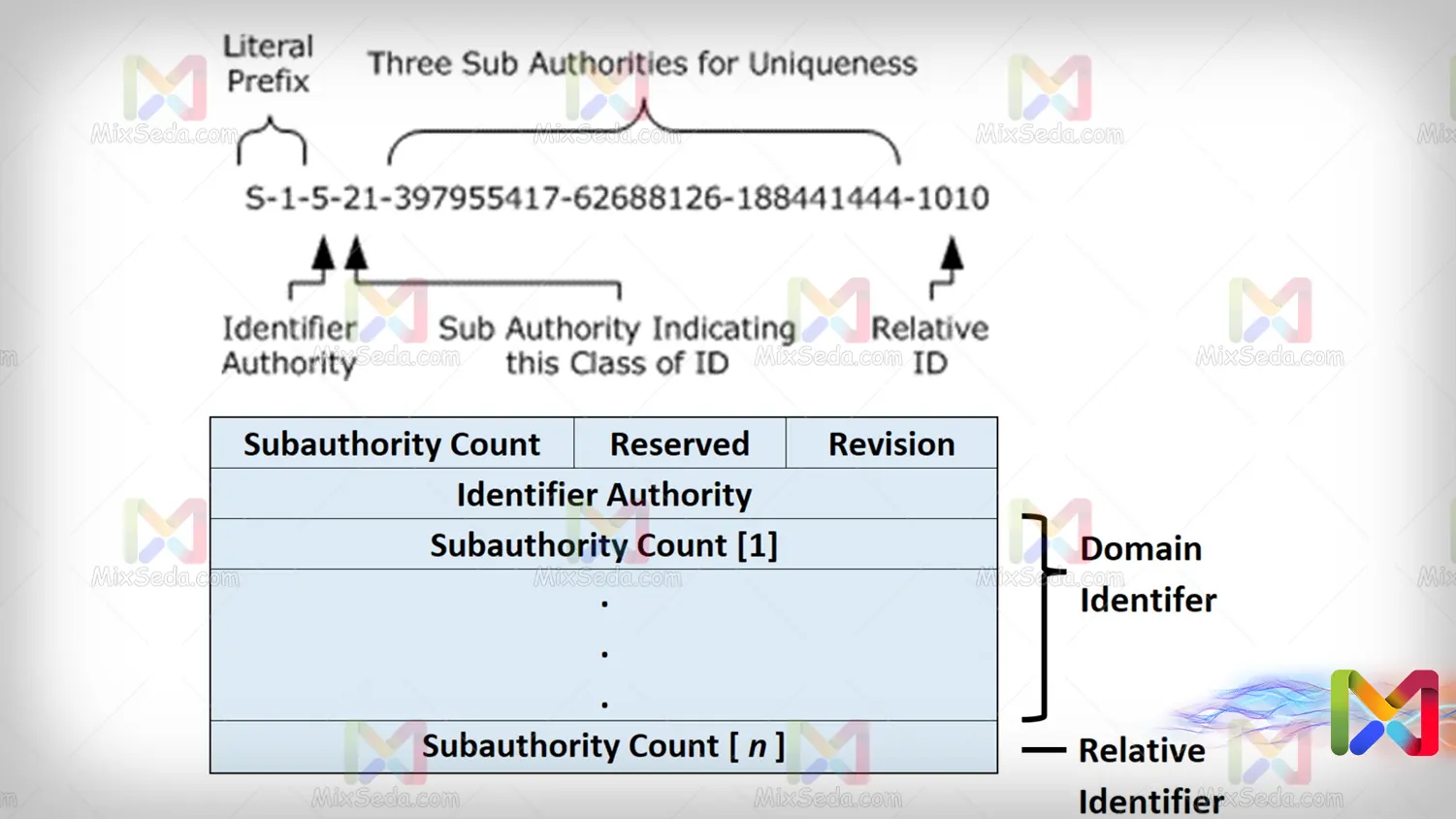
In the RIDs we also have a series of predefined values. For example, the admin user uses a RID of 500 on all computers. Or, for example, the Guest user uses RID 501 by default on all computers.
By using the following command and entering it in CMD, you can see the list of all user accounts on your system along with their SIDs:
wmic useraccount get name, sid
SIDs are designed in such a way that it is almost impossible to find two users with the same SID on a computer network.
But it is possible to capture an image of a networked system and intentionally create similar SIDs. Of course, this will cause a lot of problems in your network. In the future, I will teach you what to do to change the SID if such an incident occurs.
وظیفه SID
In general, in Microsoft networks, all users are identified by SID. When you intend to go through the authentication process, in the first step you are sending your username and password to a server.
therefore the server that intends to provide you with the service; Create a token for yourself that includes username, SID, and even the group the user is a member of. The service provider's server then sends this token to the client so that it can get the desired service by using it.
The token is valid for a certain period of time, and after that period the client must repeat the authentication process to authenticate and continue the service. We will not talk about tokens here. You can read about special identity groups for a better understanding of SIDs.
You could really talk about SIDs and how they work for hours, and when I started this article I didn't think it would be that long. If you have any questions about the above, ask in the comment section and I'll get back to you.
